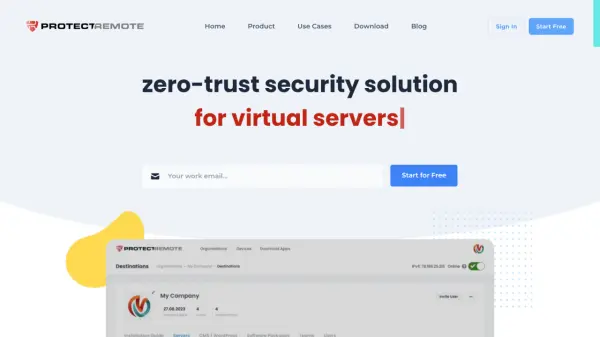
What is Protect Remote?
Protect Remote is a cybersecurity platform that leverages advanced technology to create a secure, zero-trust network between teams and their critical resources. Designed for flexibility, it enables administrators to restrict access to servers, databases, APIs, and web applications so that only authorized users can reach designated endpoints from any location, without the need for static IP addresses.
With robust protections against common threats like RDP, SSH, and port attacks, Protect Remote blocks unwanted requests and strengthens your security posture. The solution seamlessly integrates with development environments, WordPress sites, and external services, making it suitable for a wide range of remote work and server protection scenarios while enhancing your organization’s cybersecurity with minimal complexity.
Features
- Zero-Trust Security: Permits only authorized users to access protected resources from any location.
- Static IP Bypass: Eliminates the dependence on static IPs for access control.
- Multi-Protocol Protection: Secures RDP, SSH, FTP, APIs, and web application endpoints.
- Granular User Permissions: Define and manage user-level access for enhanced security.
- WordPress Security: Restricts admin panel and sensitive URL access for WordPress sites.
- Easy Integration: Works alongside existing infrastructures like VPNs.
- Development Environment Access: Securely opens databases, code repositories, and cache servers for development teams.
Use Cases
- Prevent unauthorized access to remote desktop sessions (RDP).
- Safeguard sensitive APIs by allowing only whitelisted partners.
- Secure SSH ports on Linux servers for specific team members.
- Restrict access to WordPress admin panels for enhanced website security.
- Allow development teams secure remote access to databases and internal services.
- Protect web applications exposed to the internet from potential hacking attempts.
- Block port and brute-force attacks targeting server resources.
FAQs
-
Do I need a static IP address to use Protect Remote?
No, Protect Remote provides secure access control without requiring static IP addresses. -
Which services can be protected with Protect Remote?
The platform secures remote desktops, SSH, FTP, APIs, WordPress admin panels, and other web applications. -
Is there a free trial available?
Yes, users can try Protect Remote for free for 30 days without providing a credit card. -
Can I manage user permissions for resource access?
Yes, administrators can define and control which users are allowed to access specific resources.
Related Queries
Helpful for people in the following professions
Protect Remote Uptime Monitor
Average Uptime
0%
Average Response Time
0 ms
Featured Tools
Join Our Newsletter
Stay updated with the latest AI tools, news, and offers by subscribing to our weekly newsletter.