What is Sentrycs?
Sentrycs provides advanced counter-drone solutions designed to address the complexities of modern airspace security. Utilizing cutting-edge autonomous C-UAS technology based on Protocol Manipulation (Cyber RF), the system offers effective and reliable performance. Sentrycs focuses on delivering effortless and cost-effective solutions to protect critical assets and areas from evolving drone threats.
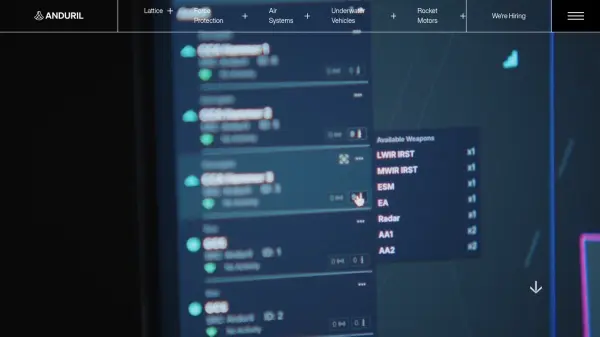
The system operates by passively detecting, tracking, and identifying unauthorized drones, even locating their operators. It features autonomous monitoring and alerting capabilities, functioning 24/7, even in challenging conditions like nighttime or beyond visual line of sight (BVLOS). Upon detection and identification, Sentrycs offers multiple mitigation options, including landing the drone safely, sending it back to its origin, or enforcing geofencing, all managed within a single system that includes a Command and Control (C2) module.
Features
- Autonomous Detection: Passively detects an unlimited number of drones 24/7, even during nighttime & BVLOS operations.
- Precise Tracking: Monitors drone height, speed, and location, including the remote control's last known position.
- Detailed Identification: Provides user-level identification including drone vendor, type, and serial number.
- Protocol Manipulation Mitigation: Offers safe mitigation options (safe landing, return-to-home, geofencing) by disconnecting the drone from its remote control without interference or collateral damage.
- Sentrycs Horizon Engine: Incorporates a self-learning engine to combat DIY drones.
- Multiple Deployment Kits: Available in fixed, portable, and vehicle-mounted configurations for seamless deployment.
- Passive Operation: Works without emitting signals, avoiding interference.
- Friend vs. Foe Identification: Capable of distinguishing authorized drones from threats.
Use Cases
- Securing airports from unauthorized drone activity.
- Protecting borders against drone intrusions.
- Safeguarding prisons from drone-based contraband delivery or surveillance.
- Defending critical infrastructure (e.g., power plants, data centers) from drone threats.
- Ensuring safety during mass events by monitoring and neutralizing rogue drones.
- Providing law enforcement with tools to manage drone-related incidents.
- Equipping defense and special forces with advanced C-UAS capabilities.
- Assisting first responders in managing airspace during emergencies.
FAQs
-
How does Sentrycs mitigate drone threats?
Sentrycs uses protocol manipulation to disconnect the drone from its remote control. It then offers options to land the drone safely in a designated area, send it back to its home location, or enforce geofencing. -
Can Sentrycs operate without causing interference?
Yes, Sentrycs operates passively and uses protocol manipulation for mitigation, ensuring no interference or collateral damage. -
What kind of information does Sentrycs provide about detected drones?
Sentrycs provides user-level identification, including the drone vendor, drone type, serial number, and the location of both the drone and its remote control (last known location). -
Is Sentrycs difficult to set up?
No, Sentrycs features seamless deployment with plug-and-play setup that takes minutes. -
Can Sentrycs handle multiple drones at once?
Yes, the system can detect an unlimited number of drones and keeps tracking other drones even while performing mitigation on one.
Related Queries
Helpful for people in the following professions
Sentrycs Uptime Monitor
Average Uptime
98.85%
Average Response Time
1104.77 ms
Featured Tools
Join Our Newsletter
Stay updated with the latest AI tools, news, and offers by subscribing to our weekly newsletter.