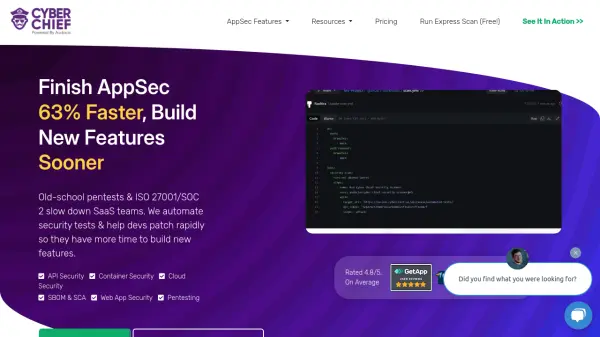
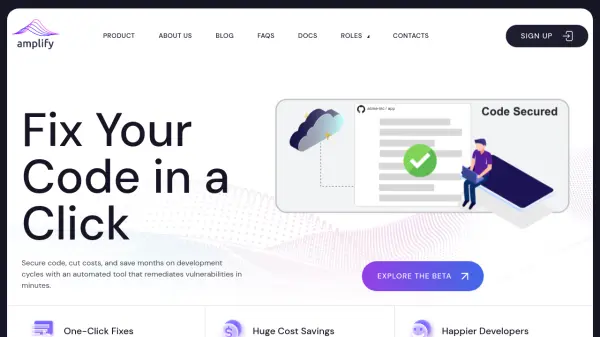
What is Cyber Chief?
Cyber Chief offers a unified platform consolidating multiple application and cloud security tools to streamline vulnerability management for Software-as-a-Service (SaaS) teams. It automates security testing across various components, including APIs, web applications, cloud configurations (AWS, GCP, Azure), containers, and software dependencies (SCA/SBOM). This automation aims to help development teams identify and fix security vulnerabilities significantly faster, thereby reducing the time spent on security tasks and allowing more focus on developing new product features.
The platform integrates directly into existing development workflows and CI/CD pipelines such as Jenkins, Azure DevOps, Github, and Gitlab, embedding security testing as a natural part of the software development lifecycle (SDLC). Beyond automated scanning, Cyber Chief provides developers with detailed remediation guidance and access to on-demand security coaching from experts. It also facilitates penetration testing as a service and generates downloadable security reports and verifiable certificates to help businesses build trust with customers and meet compliance requirements.
Features
- Bolt API Security Tool: Updates API catalogues and fixes API security vulnerabilities.
- Web App Security Tool: Speeds up vulnerability patching behind web app login pages.
- Raider Cloud Security Posture Management (CSPM): Fixes cloud security misconfigurations on AWS, GCP & Azure.
- Raider Container Security: Scans containers and Kubernetes for code-level security issues before production.
- Raider SCA & SBOM Tool: Exposes insecure dependencies and generates signed Software Bill of Materials (SBOMs).
- Pentesting-As-A-Service: Offers enhanced penetration tests to find business-logic vulnerabilities.
- CI/CD Integration: Integrates with Jenkins, Azure DevOps, Github, Gitlab, Jira for seamless security testing in the SDLC.
- On-Demand Security Coaching: Provides human expert support for developers.
- Automated Reporting & Certification: Generates downloadable reports and verifiable security certificates.
Use Cases
- Automating application security testing for SaaS companies.
- Integrating security scanning into the software development lifecycle (SDLC).
- Identifying and fixing vulnerabilities in APIs, web applications, cloud infrastructure, and containers.
- Managing software supply chain security with SCA and SBOM generation.
- Accelerating vulnerability remediation with detailed guidance and expert coaching.
- Performing regular penetration testing to uncover complex vulnerabilities.
- Demonstrating security posture to customers, investors, and auditors.
- Reducing reliance on dedicated security teams for development support.
Related Queries
Helpful for people in the following professions
Cyber Chief Uptime Monitor
Average Uptime
99.86%
Average Response Time
235.83 ms
Featured Tools
Join Our Newsletter
Stay updated with the latest AI tools, news, and offers by subscribing to our weekly newsletter.