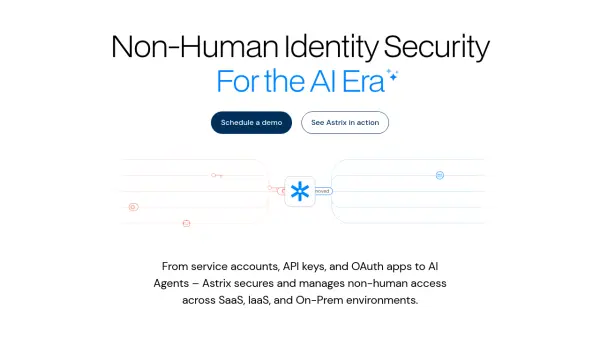
What is Astrix Security?
By focusing on the entire lifecycle of non-human identities, from creation to decommissioning, Astrix helps organizations enforce policies, automate remediation, and ensure compliance with regulatory requirements. It specifically addresses the risks associated with AI agents, which often require privileged access, and helps secure third-party integrations and cloud environments, mitigating threats like third-party breaches and anomalous NHI activity.
Features
- Real-time discovery of non-human identities: Continuously identify all NHIs across environments.
- Posture Management: Prioritize NHI risks and improve security posture.
- Anomaly Detection: Detect & respond to anomalous NHI and AI Agent activity.
- Auto-Remediation: Automate remediation using integrations and playbooks.
- Next-gen Secret Scanning: Map exposed secrets and facilitate rotation.
- Agentic AI Access Governance: Govern AI Agents through visibility, context, and access controls.
- NHI Lifecycle Management: Manage NHIs from provisioning to decommissioning.
- Centralized Secret Management: Manage secrets across vaults and cloud environments.
Use Cases
- Govern and enforce policies across the NHI attack surface.
- Securely adopt and monitor AI agents.
- Manage the complete lifecycle of Non-Human Identities.
- Detect and respond to suspicious NHI activity and third-party breaches.
- Centralize secret management across different vaults and cloud platforms.
- Meet NHI regulatory compliance requirements with continuous monitoring and reporting.
- Extend IAM & ITDR programs to cover non-human identities.
- Secure third-party app integrations and vendor connections.
- Secure non-human access in cloud engineering environments (AWS, GCP, Azure, GitHub).
Related Queries
Helpful for people in the following professions
Astrix Security Uptime Monitor
Average Uptime
100%
Average Response Time
261.47 ms
Featured Tools
Join Our Newsletter
Stay updated with the latest AI tools, news, and offers by subscribing to our weekly newsletter.